
From Crime Scene to Lab: Top Forensics Tools Explained
Why Forensics Tools Are Essential for Modern Investigations
Forensics tools are specialized equipment and software used to collect, preserve, analyze, and present evidence in criminal investigations and legal proceedings. These tools span from physical crime scene equipment like tweezers and barrier tape to advanced digital platforms like Autopsy and EnCase.
Essential Categories of Forensics Tools:
- Crime Scene Tools: Evidence collection kits, measuring devices, photography equipment
- Digital Forensics Software: Autopsy, EnCase, FTK for analyzing computers and mobile devices
- Memory Analysis Tools: Volatility, Magnet RAM Capture for examining system memory
- Network Forensics: Wireshark, SNORT for investigating network traffic
- Mobile Forensics: Cellebrite UFED, Oxygen Detective for smartphone analysis
The forensics landscape has evolved dramatically since the 1980s, when investigators relied on basic "live analysis" using general-purpose tools. Today's investigations demand specialized equipment that can handle everything from BitLocker-encrypted drives to drone flight logs, while maintaining the chain of custody that courts require.
Modern forensics follows a clear workflow: evidence collection at the crime scene, secure transportation to the lab, detailed analysis using specialized tools, and finally presentation in court. Each step requires different tools - from simple collection implements to sophisticated software platforms that can process terabytes of data.
The integration of digital and physical forensics has created new challenges. Investigators now need tools that can extract deleted files from smartphones, analyze network traffic patterns, and correlate digital timestamps with physical evidence - all while ensuring the integrity needed for legal proceedings.
As we've seen through our work at American Mortuary Coolers with experience supplying specialized equipment to the forensics community, the right forensics tools can make or break an investigation.
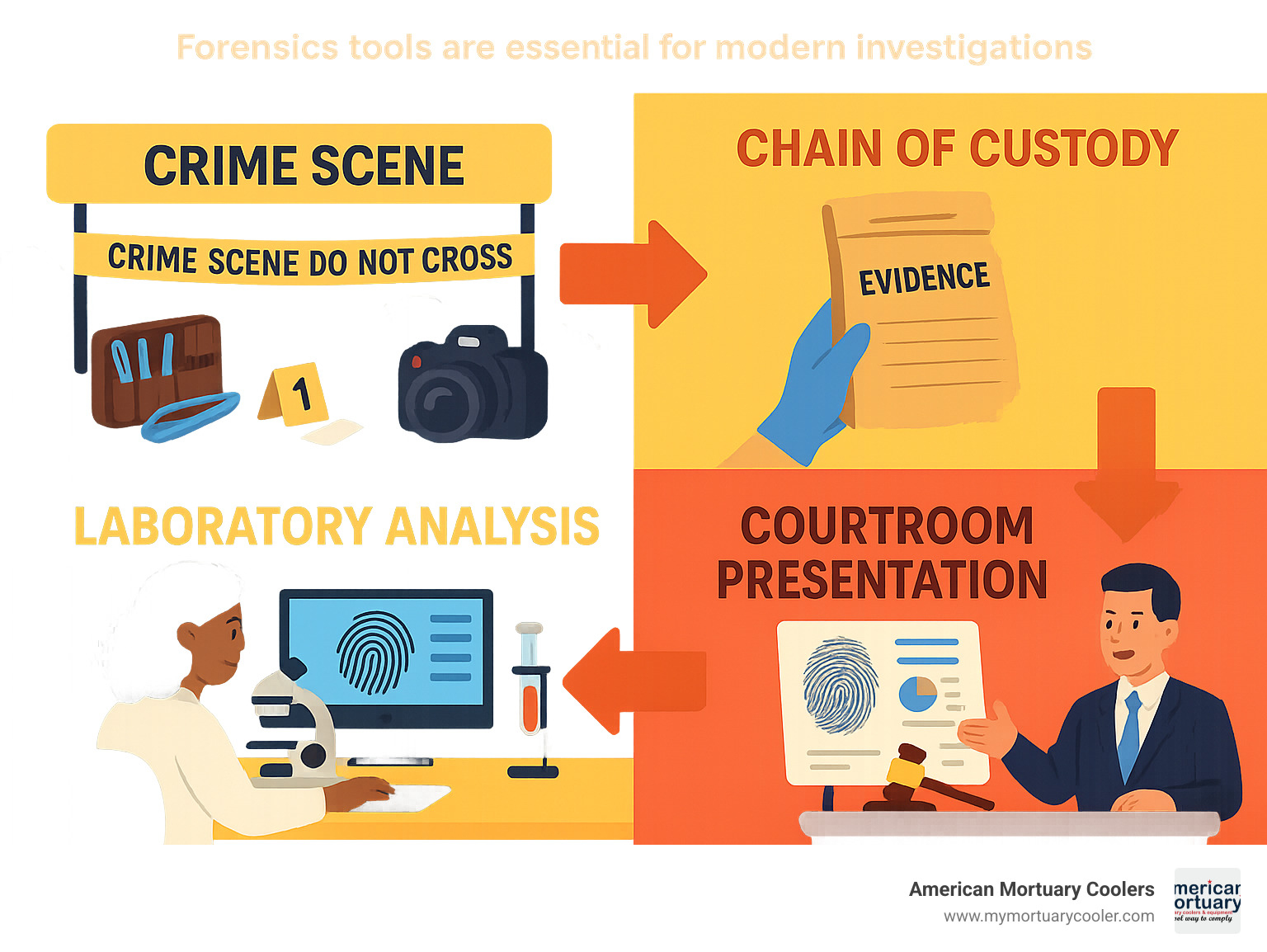
Crime Scene Essentials for Evidence Integrity
The moment investigators arrive at a crime scene, they're racing against time. Every second counts when it comes to preserving evidence that could solve a case. That's where the right forensics tools become absolutely critical - they're the difference between a rock-solid investigation and one that falls apart in court.
Securing the scene comes first, and that means barrier tape stretched around the entire area. Once the perimeter is established, investigators can begin the careful process of evidence collection using specialized tools designed for precision work.
Modern crime scenes require both traditional and high-tech approaches. Specialized tweezers and scalpels handle delicate trace evidence like fibers or paint chips, while gun shot residue collection kits capture microscopic particles that can link suspects to firearms. For larger scenes, Leica laser scanners create incredibly detailed 3D maps that preserve spatial relationships.
Trace evidence collection demands the most careful attention. These specialized kits contain everything from adhesive carbon stubs to sterile scrapers, each designed to collect specific types of microscopic evidence without cross-contamination.
Documentation tools complete the crime scene toolkit. Sketch templates help investigators create accurate diagrams, while standardized crime scene notebooks ensure nothing gets overlooked. These seemingly basic forensics tools often prove their worth in court, where detailed documentation can make or break a case.
More info about crime scene investigators
Building Your Field Kit
Every crime scene investigator develops their own system for organizing field equipment, but certain essentials appear in every well-prepared kit. Multiple sizes of nitrile gloves prevent contamination between evidence samples, while sterile cotton swabs collect biological evidence safely. A comprehensive crime scene notebook ties everything together with proper documentation.
Organization matters tremendously when you're working under pressure. Evidence containers need clear labeling and proper sealing to maintain chain of custody. Many experienced investigators swear by color-coded systems - it's much easier to grab the right container when red means biological evidence, blue handles trace materials, and clear containers hold items requiring visual inspection.
Specialized collection tools vary depending on the type of case you're working. Blood identification kits contain presumptive testing materials that can quickly confirm whether stains are actually blood. Bullet hole test kits help determine trajectory and impact patterns.
First Steps With Physical Forensics Tools
Those first moments at a crime scene set the tone for the entire investigation. Investigators must secure the perimeter with barrier tape while simultaneously conducting an initial assessment to identify potential evidence.
Photography equipment becomes your primary documentation tool from the moment you arrive. Digital cameras equipped with macro lenses capture both wide shots showing the overall scene and detailed close-ups of individual evidence items.
Chain of custody documentation starts immediately and never stops. Every piece of evidence gets photographed in its original location, carefully collected using appropriate tools, sealed in proper containers, and logged with detailed information about who collected it, when, and under what circumstances.
At American Mortuary Coolers, our work with funeral homes has taught us the critical importance of proper evidence handling and storage throughout investigative processes.
Digital Forensics Tools: Core Platforms & Suites
When investigators need to dive deep into computers, phones, and other digital devices, they turn to specialized forensics tools that can uncover evidence criminals thought they'd erased forever. These software platforms have become the digital detectives of our time, revealing secrets hidden in the depths of hard drives and memory cards.
Autopsy has earned its reputation as the go-to choice for investigators working with tight budgets. This open-source powerhouse, built on The Sleuth Kit library, gives investigators a user-friendly interface for examining everything from laptops to smartphones. What makes Autopsy particularly impressive is its ability to start showing keyword results within minutes, even while it continues analyzing gigabytes of data in the background. You can learn more about this powerful tool at Autopsy.
For agencies that need enterprise-level support and features, EnCase and Forensic Toolkit (FTK) represent the premium end of digital forensics. EnCase has dominated the field so thoroughly that SC Magazine named it "Best Computer Forensic Solution" for ten straight years. Meanwhile, FTK excels at processing massive amounts of data, making it ideal for complex investigations involving multiple devices and suspects.
Linux-based forensic distributions like CAINE and SIFT offer complete investigative environments on a single bootable drive. These distributions turn any computer into a temporary forensic workstation.
Imaging & Acquisition Forensics Tools
Before any digital detective work can begin, investigators must create perfect copies of the evidence. FTK Imager has become the gold standard for creating these forensic copies. This free tool makes bit-perfect images of hard drives, SSDs, and even mobile devices while generating hash values that prove the copy matches the original exactly.
Guymager offers Linux users a friendlier alternative with real-time progress updates and multiple output formats. dc3dd rounds out the imaging toolkit with command-line power for advanced users.
Triage & Timeline Forensics Tools
Modern digital investigations can involve terabytes of data - more information than investigators could examine in months of manual work. Triage tools act like smart filters, automatically identifying the most promising evidence so investigators can focus their time where it matters most.
Cyber Triage transforms overwhelming data dumps into manageable investigations. Using more than 40 different analysis engines, it automatically flags suspicious files, unusual network connections, and potential evidence of criminal activity.
Magnet AXIOM excels at connecting the dots between different devices and data sources. When suspects use multiple phones, computers, and cloud accounts, AXIOM can correlate evidence across all these sources to build comprehensive timelines of criminal activity.
aLEAPP specializes in Android device analysis, parsing through the complex file structures that modern smartphones create. This tool can extract everything from deleted text messages to location histories.
Exploring Essential Forensic Tools and Equipment
Specialized Forensics Tools for Memory, Network & Mobile Analysis
Modern cybercriminals have gotten smarter about covering their tracks. They know that traditional forensics tools focus on hard drives and file systems, so they've learned to operate in the shadows - using memory-only attacks, encrypted communications, and sophisticated mobile apps. That's where specialized analysis tools come into play.
Memory forensics has become the digital equivalent of dusting for fingerprints in places criminals thought they'd wiped clean. Tools like Volatility can capture what was happening in the computer's memory - running programs, network connections, even encryption keys that open up protected files. This Python-based framework works across different operating systems and has solved cases that seemed impossible just a few years ago.
MAGNET RAM Capture makes memory collection straightforward, even for investigators who aren't computer experts. It creates exact copies of system memory that can be analyzed later, preserving evidence that would otherwise vanish the moment someone turns off a computer.
Network investigations require a different approach entirely. Wireshark has become the gold standard for analyzing network traffic - it's used by everyone from government agencies to private corporations. SNORT takes this a step further by watching network traffic in real-time, alerting investigators when suspicious activity occurs.
Mobile device analysis presents some of the biggest challenges in modern forensics. Tools like Cellebrite UFED and Belkasoft X can bypass locks and extract data from thousands of different devices, uncovering text messages, photos, location data, and app communications that criminals thought were private.

Memory & Live-Response Forensics Tools
Volatile memory analysis captures the digital equivalent of a crime scene before it disappears. When a computer is running, its memory contains a treasure trove of information - active programs, network connections, and decrypted data that might be locked away on the hard drive.
Redline brings user-friendly interfaces to memory analysis. Developed by FireEye, this tool makes complex memory forensics accessible to investigators who need results quickly.
DFIR ORC excels in incident response scenarios. This tool can collect evidence from live systems without installing anything, making it perfect for situations where investigators need to gather information quickly without alerting suspects.
Network & Cloud Forensics Tools
Network forensics helps investigators understand the digital conversations happening between computers. NetworkMiner specializes in reconstructing network communications. It can pull files, images, and messages out of network traffic, essentially rebuilding the digital crime scene from captured network data.
Nagios provides the early warning system that many investigations need. By monitoring network activity in real-time, it can alert investigators to suspicious behavior before criminals complete their activities.
Hansken represents the cutting edge of forensic search technology. This platform can analyze massive amounts of data incredibly quickly - reportedly 48 times faster than previous tools.
Bulk Extractor takes a unique approach by ignoring file system structures entirely. Instead of trying to understand how files are organized, it scans raw data for recognizable patterns like email addresses, credit card numbers, and URLs.
Mobile & IoT Forensics Tools
Mobile forensics has become one of the most important areas of digital investigation. Cellebrite UFED has become the Swiss Army knife of mobile forensics. This hardware-software combination can extract data from thousands of different devices, including phones with cracked screens, dead batteries, or security locks.
Oxygen Forensic Detective excels at cloud-based evidence collection. Many people don't realize that their smartphones continuously back up data to cloud services. This tool can access those backups, often recovering messages and photos that were deleted from the physical device months ago.
The emergence of drone forensics shows how quickly this field evolves. Tools that can parse DJI drone flight logs extract GPS coordinates, flight paths, and camera settings.
As we've learned from our work with the forensics community at American Mortuary Coolers, the right specialized tools can uncover evidence that seemed impossible to find.
Choosing, Testing & Admitting Forensics Tools in Court
Selecting the right forensics tools isn't just about finding software that works - it's about choosing tools that will hold up under the intense scrutiny of cross-examination. When a defense attorney questions your methods, you need rock-solid validation behind every tool you used.
The NIST Computer Forensics Tool Testing Program has become the gold standard for tool validation. Their comprehensive testing puts tools through rigorous paces, examining everything from accuracy to reliability under various conditions. The NIST Tool Catalog lets investigators search for validated tools by specific capabilities.
FEMA's Authorized Equipment List takes a different approach, focusing on procurement standards for law enforcement agencies. Under category 05HS-00-FRNS, digital forensics tools must meet federal requirements for reliability and effectiveness.
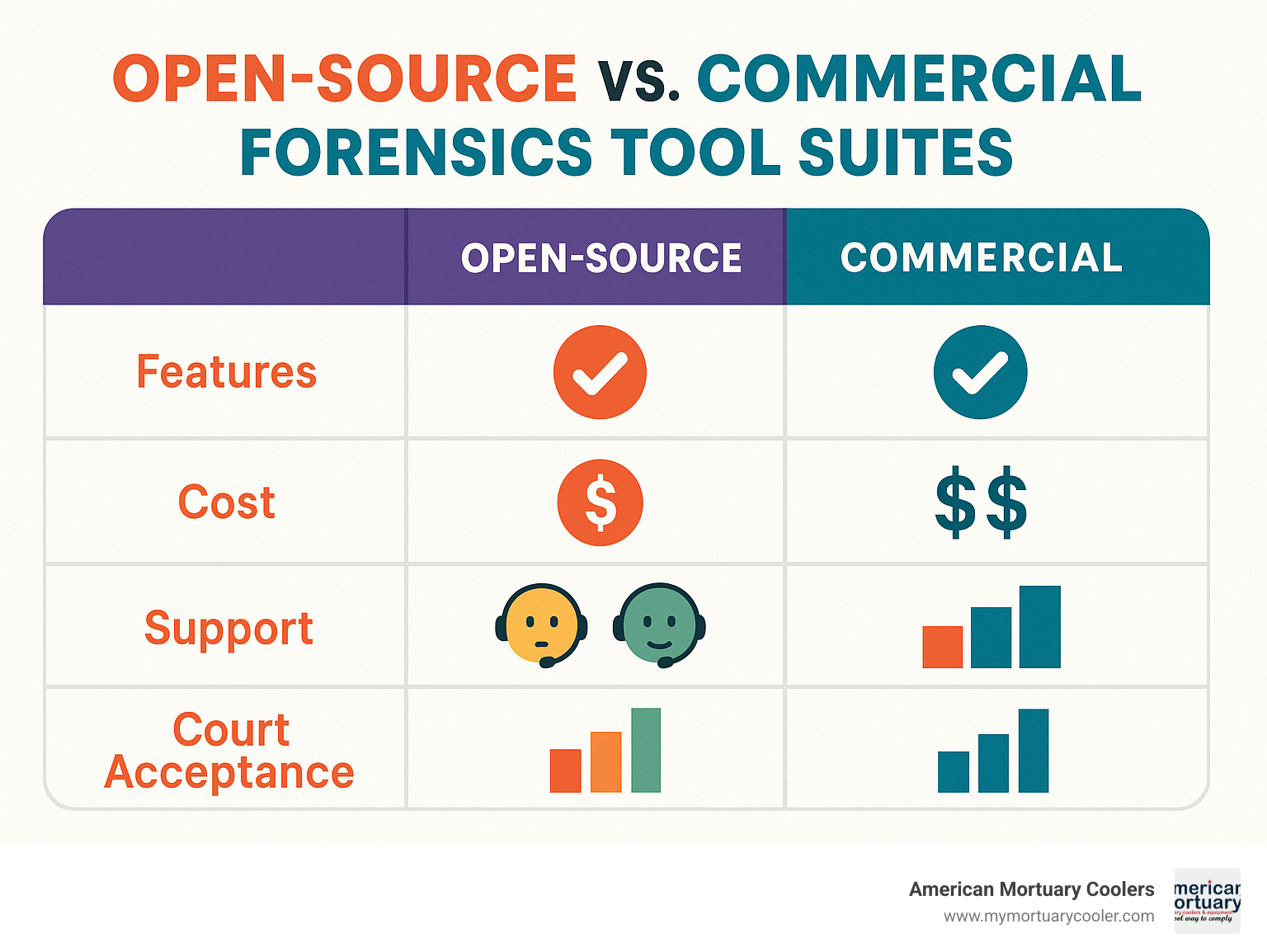
The eternal debate between open-source versus commercial tools isn't just about budget - it's about support, validation, and legal acceptance. Open-source tools like Autopsy offer impressive capabilities without licensing costs, but they require more technical expertise. Commercial suites provide dedicated support and extensive documentation.
Hash verification serves as your mathematical insurance policy. Every reputable forensic tool automatically calculates MD5 and SHA-256 hash values, creating digital fingerprints that prove evidence hasn't been tampered with.
Ensuring Evidence Integrity With Forensics Tools
Write blockers represent one of the most important innovations in digital forensics. These hardware devices act like one-way valves, allowing forensics tools to read data while physically preventing any writes to the original evidence.
Documentation requirements extend far beyond just recording what you found. Courts want to know which tools you used, what versions, how they were configured, and whether they've been properly validated.
Modern investigations demand validation testing before any tool touches actual case evidence. Smart investigators maintain test datasets with known results, running new tools against these benchmarks to verify accuracy.
Chain of custody in the digital field requires meticulous record-keeping. Every time evidence changes hands, gets analyzed, or moves between systems, that transfer must be documented.
Future Trends in Forensics Tools
Artificial intelligence is quietly revolutionizing forensic analysis behind the scenes. AI-powered forensics tools can now automatically identify relevant evidence, classify thousands of images in minutes, and even detect sophisticated deepfakes.
Software-as-a-Service platforms are changing how forensic labs operate. Cloud-based tools offer automatic updates and unlimited processing power, but they raise important questions about data security and jurisdiction.
Blockchain evidence lockers might sound like science fiction, but they're already being tested in forward-thinking jurisdictions. These systems create tamper-proof records of evidence handling, potentially solving long-standing chain of custody challenges.
The future promises even more sophisticated tools, but the fundamentals remain unchanged. Whether you're using cutting-edge AI or traditional hash verification, the goal stays the same - presenting reliable evidence that serves justice and stands up in court.
Frequently Asked Questions about Forensics Tools
When investigators first start working with forensics tools, they often have similar questions about which tools work best and how to ensure their evidence will hold up in court.
What categories of forensics tools do investigators rely on most?
Most investigators build their toolkit around five core categories that handle different aspects of evidence collection and analysis.
Crime scene collection tools form the foundation of any investigation. These range from simple items like evidence bags and tweezers to sophisticated equipment like 3D laser scanners that can map an entire crime scene.
Digital forensics platforms do the heavy lifting when it comes to computer evidence. Tools like Autopsy, EnCase, and FTK can dig through massive hard drives to recover deleted files, trace internet activity, and crack encrypted storage.
Memory analysis tools like Volatility tackle a special challenge - capturing evidence that disappears when you turn off a computer. This volatile memory often contains crucial information like passwords, running programs, and network connections.
Network forensics utilities help investigators understand how data moved between systems. Wireshark, for example, can analyze network traffic to show exactly what information was transmitted and when.
Mobile device extraction tools round out the toolkit by handling smartphones and tablets. With tools like Cellebrite UFED, investigators can extract text messages, photos, and app data even from locked devices.
How do open-source forensics tools compare to commercial suites?
The choice between free and paid forensics tools often comes down to your specific needs and budget constraints.
Open-source tools like Autopsy pack impressive capabilities without the price tag. Autopsy includes all the core features you'd find in expensive commercial tools, plus specialized functions like web artifact analysis. The catch? You'll need more technical knowledge to set them up and troubleshoot issues.
Commercial platforms like EnCase justify their cost through comprehensive support and training programs. EnCase has earned SC Magazine's top forensics award for ten straight years, which speaks to its reliability.
The cost difference can be substantial. Open-source tools eliminate licensing fees that can run thousands of dollars per user, but they may require hiring more technically skilled staff.
Court acceptance really depends on how well you validate and document your tools, not whether they're free or expensive. Both open-source and commercial tools can be admissible if you can demonstrate they produce reliable results through proper testing.
What standards keep evidence collected with forensics tools admissible?
Getting evidence admitted in court requires following established standards that prove your forensics tools and methods are scientifically sound.
NIST standards provide the gold standard for forensic tool validation through their Computer Forensics Tool Testing Program. This program establishes clear criteria for testing tool accuracy and identifying limitations.
ISO/IEC 27037 offers international guidelines that help ensure your procedures meet global best practices. This standard covers everything from tool validation to evidence handling.
Daubert criteria in US courts require that scientific evidence be based on reliable methods. For forensic tools, this means demonstrating that they've been properly tested, peer-reviewed, and accepted by the scientific community.
Documentation requirements tie everything together by creating a paper trail that shows proper procedures were followed. This includes records of tool validation, detailed evidence handling logs, and step-by-step analysis documentation.
Conclusion
The journey through forensics tools reveals just how far criminal investigations have traveled from the simple fingerprint dusting of decades past. Today's investigators work with everything from basic evidence collection tweezers to sophisticated AI-powered analysis platforms that can process terabytes of data in hours rather than weeks.
The right tools make all the difference between a case that goes cold and one that leads to justice. Whether you're using the open-source power of Autopsy to recover deleted files or deploying Cellebrite's mobile extraction capabilities to open up a smartphone, success depends on understanding both what your tools can do and where their limits lie.
At American Mortuary Coolers, we've spent years working alongside the forensics community across Tennessee, Georgia, Illinois, and beyond. Our experience supplying specialized equipment has taught us something important: proper evidence handling doesn't end at the crime scene. From the moment evidence is collected until it reaches the courtroom, every step requires the right equipment and careful attention to detail.
Technology keeps pushing forward, and the forensics field moves with it. AI triage systems are already helping investigators sort through massive datasets, while blockchain evidence lockers promise tamper-proof storage solutions. Cloud-based platforms offer new possibilities for collaboration and analysis, though they bring their own security challenges.
But here's what hasn't changed: the fundamentals still matter most. Proper collection techniques, careful documentation, and maintaining chain of custody remain the bedrock of successful investigations. The fanciest software in the world won't help if the evidence was contaminated at the scene or if the documentation doesn't meet court standards.
Staying current with forensics tools means more than just buying the latest equipment. It requires ongoing training, regular validation testing, and understanding how new technologies fit into established legal frameworks. The investment pays off when that crucial piece of evidence holds up in court and justice is served.
From our facilities across the country, we continue supporting investigators who dedicate their careers to finding truth in the most challenging circumstances. The pursuit of justice depends on having the right tools - and knowing how to use them properly.
More info about American-mortuary-coolers-the-leading-supplier-of-mortuary-coolers-funeral



